Every mobile phone has a SIM – a chip that identifies the phone as yours on the network. It can be a removable card or an eSIM that stays inside. But either way, this “subscriber identity module” pairs your phone number to your device.
Some thieves search for ways to steal your phone number. And they don’t have to physically have your phone.
First, they target a person with valuable online accounts. These could include a financial account or a social media account with a large following.

If you become a target, a thief gathers information about you like email, home address and phone numbers. They may try to trick you into revealing information about yourself through phishing or social engineering. But they may also get the information with internet searches or from social media.
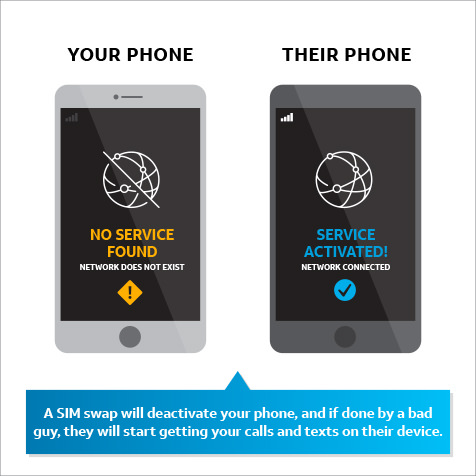
Once he has the information, the thief may call your phone carrier, pretending to be you, and attempt a “SIM swap.” He may convince your mobile service provider to link your mobile service with the SIM card of a mobile phone in the thief’s possession. If successful, the mobile network will start sending calls and SMS text messages to the new SIM card – which is really the thief’s phone.
This will deactivate your phone, and the thief will start getting your calls and SMS texts on his device, including authentication texts and one-time PINs. If you use these verification methods, the thief may be able to reset your passwords and gain access to your financial or social media accounts.
What AT&T is doing
We are working hard with other major phone carriers and business partners to help prevent unauthorized SIM swaps. However, the thieves constantly change their tactics. So, we are continually enhancing safety measures, including:
- Building tools to make it harder for someone to pretend to be you
- Helping companies flag suspected thieves during online transactions by strengthening text-authentication tools
- Training employees and customers to better recognize impersonation attempts
- Expanding fraud detection and support
- Applying advanced technology to detect and stop suspected unauthorized SIM swaps
- Working closely with law enforcement to identify these criminals and bring them to justice
What can you do?
These scams often target high-profile individuals and people believed to have big financial accounts. But it could happen to anyone. Here are a few tips to help avoid having your number and your accounts taken over:
- Consider using account authentication measures that don’t depend on your phone number. For instance, many online accounts now allow options like authentication apps. For high-value accounts, you could consider a hardware authentication token – such as a keychain fob that produces a new code when you press it.
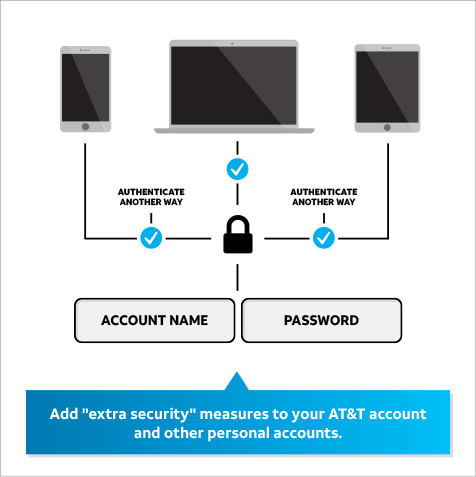
- Add "extra security" measures to your AT&T Wireless accounts. If you create a unique passcode on your AT&T account, in most cases we'll require you to provide that passcode before any significant changes can be made, including porting initiated through another carrier. You can learn more about passcodes at this link.

- Don't share personal information online. Don't post, or at least carefully limit, information on social media that a thief could use to gain access to your accounts or convince someone he is you. This includes legal names, birth dates and information that could be an answer to a security question, such as a pet's name, your best friend or high school mascot.
- Keep your personal email in box clean. Delete phone bills, bank statements and other emails that may include personal information. Don't store passwords, passcodes or pins in unencrypted or unsecure email accounts. This will help reduce the risk of your sensitive information falling into the wrong hands.
- Be careful about sharing your mobile phone number. Consider using a different number, such as a landline, with businesses like grocery stores and dry cleaners. Limit sharing your mobile number anywhere it might be posted publicly or to many people, such as on social media, email signatures, and phone lists.
- Learn about the security measures available and make sure you are using the most secure authentication methods.
- If you want to be particularly careful, store cryptocurrency in “cold storage” – an environment without online access.
- Don’t store cryptocurrency wallet credentials online. Instead, write them down and keep them in a secure physical location.
- When choosing financial investments and services, consider that some are protected from theft and fraud, others are not. For example, cryptocurrency accounts are not insured from theft like other types of traditional financial accounts. If cryptocurrency is stolen from you, it most likely cannot be recovered.
If you believe your SIM card has been swapped without your consent, report it to your carrier right away.
You can also refresh yourself on our Cyber Aware tips to protect yourself online.